Memory Forensics
Today, I will explain you what memory Forensics
is… Now this area is referred to as memory analysis. In this area, it
is important to do your analysis of volatile data in a computer’s memory
dump.
Security Professionals are able to conduct such memory dump to
investigate malware or other being injected process.
We will be able to investigate and doing our forensics to catch
malicious behaviours that do not leave easily detectable tracks on hard
drive.
Acquisition Process
When we hear this term, we should consider this as the process of copying the contents of volatile memory(RAM). In order to have a good understanding of the process its important to learn some memory management principles and disiciplines. In this blogpost, we will be going to extract and dump our memory to get more familiar with the process. We will also learn a bit about live memory analysis on Windows OS. Memory live analysis has its advantages to dig deeper into memory dump. Now before diving into Rekall Project let me explain a bit more about acquisition Process.
Volatile Memory
We know that this definition has to do with Random Access Memory(RAM), which stores the code and data that the process actively access and stores. However, we ought to know that processes have not direct access to physical memory. This is because process can easily harm the operating system. RAM is defined as volatile memory because when you powered your computer on, it requires power for the data to remain accessible and when you powered your computer off, being stored will be permanently deleted. Ram can be attacked by Cold boot attack for more information you can get more from this source: https://en.wikipedia.org/wiki/Cold_boot_attack
Virtual Memory
I am not going to illustrate the usage of Virtual memory, but let me explain a bit about its skeleton. Virtual memory is a storage scheme that provides user an illusion of having a very big main memory. Which means that, the abstraction is designed to seperate the logical memory that processes work with from physical memory. I would like to say thet Virtual memory has a good usage by the OS because each process has its own virtual address space however, we ought not to forget that the size of that space is depending on the hardware architecture. You can get more information from this source:
Paging
This one will be the last one of acquisition. As a short explanation
shall be that the entire process address space is divided into blocks of
fixed size. Paging provides the
ability to virtualize the linear address space. It creates an execution
environment in which a large linear address space is simulated.
We should not forget that the Memory Manager is responsible for unloading and also freeing physical memory.
The Memory Manager is important because it also translates virtual addresses into physical address with the help of hardware.
You can get more information from this source:
https://en.wikipedia.org/wiki/Memory_paging
–> I am ready to get started with Rekall Framework We will firstly look at the source code and understanding what it does while perfoming memory analysis. Lets kick off.
Rekall Memory Forensics
Now that we have understanding about Live memory forensics lets now talk about advanced memory forensics tool called Rekall.Rekall
is a forensics Framework is a collection of memory to analyze memory
dump. Rekall is written in Python and Its a fork of Volatility.
Discover Rekall
As we are dealing with memory forensics it also important to meet
rekall structure and plugins. We need to understand the functionality.
Rekall is written in Python thus that means that we are able to read
easily the source code.
For now you can use Rekall-Github but I should not recommend it. Morevover, you will be facing issues due to the python version.
For this purpose, I will be going to use docker its more flexible and more handy.
As I mentioned earlier, when you git your repo to you /opt which is recommended. We are now analyzing the structre of this Framework.
Go to /memory-forensics/rekall/rekall-core/rekall and use ls -a command to see what kind of pluging are written in this framework.
I am not going to analyze all files however, we will analyze rekall.py, and lets understand this advanced memory forensics Framework.
At this point, we will use rekali.py to have better understanding of this code.
Well, we are interested in this part and lets view the source understandably.
We are seeing that the user_session is interacting with session.py. I am going to analyze a bit about
session.py
We are checking session.py, and immediately DeclareOption is being popped up. The session is quite simple it supports .zip, url, directory which is awesome.
My memory dump is ready to be thrown in this framework. Rekall allows us to use config.DeclareOption("-f", "--filename",help="The raw image to load.") like Volatility Framework however, Volatility does not allow me to use .mem
I mean it does not
dump the memory. Overall i do like Volatility. It is quite simple to
read and understand about this Framework as well. You can get more
information from
Rekall-Github to have better understanding.
Most importantly, let me explain a bit about scanning memory files. I am going to show you the source code of scan.py so that i can explain the code respectively
First of all, ı will not cover about profile yet because that will be my next topic that i want to cover. Lets overview this source and look at the code step by step. Its
important that you ought to understand the structure of this code for being able to write your own code. As you can see we have profile, session, adress
Of course, we need to specify our profile such that it will recognize
windows machine and to be run properly. Address space, shall be
important because, when we talk about address spacing we should consider
that
there are few different categories of address spacing but let me cover
about address space stack. The main concept is about rekall but let me give a short demonstration about volatility plugins how it looks like.
As an example, we are considering Windows System crash dump with the architecture x64
In this script I just wanted to illustrate what address space was and
what it done. Let move to our main topic Rekall. If you
understood this topic lets get started with profile mechanism
Profile Mechanism
AS I mentioned before that profile mechanism is the most important part of Rekall. In order to work with Memory forensics you have to be dealing with OS(operating system), thus its necessary to specify your operating sytstem,being able to dump your memory to be analyzed it will be important. Plugins are requesting virtual address from that dump. Rekall allows us to work with different operating system and processors which is of course predicatable. Now that we already know why we using such profile mechanisms. Lets get started with using our memory dump. You can get your own memory through virtual or your main OS.
I should say that, when i was trying to capture my own volatile memory i got a blue screen with windows error. You should be alerted. It can have to with your current CPU.
I would like to explain by this code that profile is important because,
you might be able to get a lot information from this memory. It does not
matter
what you are using it can be Volatility or Rekall. You need to specify
your own operating system. Whether you not do than it will not resolve
your problem anc will have been an issue by investigating a memory.Lets
focus on GUID
As you can see that it is trying to detect GUID this term has a functionality such that
it identifies an object such as COM interface, or a COM class object, or a manager entry point.
Which data is declared in this struct. We need to know that a GUID is
a 128-bit value consisting of one group 16 hexedecimal digits.
this code is important module = self.session.address_resolver.GetModuleByName(
self.module_name)
1. Module is declared to self session address because we need to know the exact GUID
2. if not module, then it will be redirected to error regarding collecting GUID address
Linux resolver
This plugin is written for Linux OS and as you can understand from this source code that it looking for any kernel address of your ELF file to be recognized.
Winndows resolver
Here is the source/plugin for Windows OS. You can check it out. Here you can get more information about this plugin:
Everthing is abstracted and well explained. You can get also help
from the internet. the purpose of this blog is telling you that Rekall
has a lot cons.If you get any doubts, you can always ask us for any
problem which you are facing with.
Before analyzing a dump memory let me also explain about auto profile selection
I always recommned to forensics (investigators) please do not forget to
practice and enhance your skills.
Create your own memory dump file and look for any suspicious DLL and
process injection.
It will be awesome to create your own detection system.
I hope that everything was clear and when you may not be able to read
the source code well, please then check on internet or ask us.
Profile Auto Selection
Lets remind us what profile was? Profile is where you place your operating system, architecture, version to give the information to the framework to analyze the your memory dump file. Now the most significant difference from volatility from the profile plugin, is that in rekall, the profile is in JSON format which makes us easily readable. For instance, Volatility represents a specific class defined within code based. Where Rekall represents such information in JSON format.
Rekall has another cons, such as it can be hosted in public repository because those files are just data. Rekall will simply download necessary profile from the repository when you need it or required. Now when you do own deep research it seems that Rekall has a lot of capabilities. Lets see what Rekall has for us.
Firstly, we should understand that PE header string has been controlled by this plugin. If the PE is recognized by plugin then it will continue the process.
Memory dump
Being able to run rekall, i had already mentioned about docker which should be installed. You will be facing some issues if you try to run rekall from github repositories, there will be dependencies errors.
As you can see, I pulled remnux/rekall from docker.io. The next step is:
To see the process of this container. Now it is to use this command:
Just specify your docker container and use: docker exec -it b7c98db01e8c bash
If everything is OK! lets try to use rekall -h command
So this means that everything is OK!
Being able to demonstrate rekall I am going go inject inject.dll to notepad to illustrate it properly
You should look at the process hacker or task manager to identify the PID. In my case, it was 19608 Now, we are going to be able to dump our volatile memory to be analyzed with Rekall Framework.
I am also going to disassamble this code with IDA to look at the process

Let me explain a bit about this piece of code.
WriteProcessMemory
With the WriteProcessMemory function, we write the path of our dll file
to the virtual address of the previously designed process.
VirtualAllocEx
With the VirtualAllocEx function, we allocate space before we can write
the path of our dll file to the virtual address space of the target
process.
GetProcAddress
With the GetProcAddress function, we get the address on the memory of
the LoadLibraryW function, which we will use to load our dll file to the
target process. The LoadLibraryW function is a function of the
kernel32.dll library.
Awesome. Now we are going to analyze with Rekall. First of all, you should have already dumped your volatile memory to your main OS or virtual machine to make it more easier.
- be sure that your docker is running
- when you dumped your file to the right directory
- use this command
docker exec -it rekallcontainer bash - Use this command
docker cp inject.mem rekallcontainer:/ - after entering to your docker, you should use
cd ../../../../ - use
mvcommand to /home/nonroot/files
Of course, we already know that PID of notepad 19608 lets analyze that
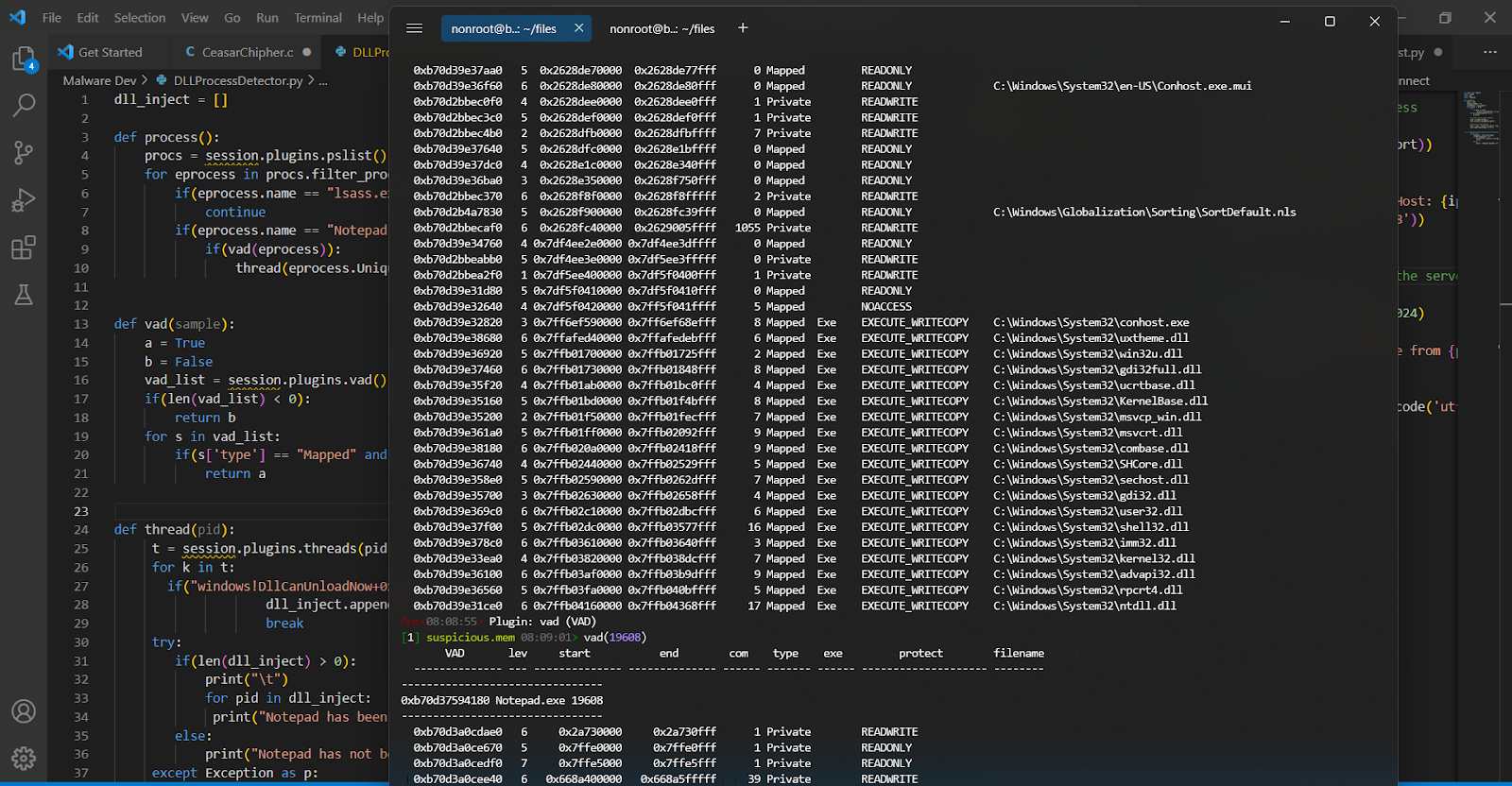
When we use ldrmodules(19608), You will see this output.It is also important to check vad
What is VAD?
VAD is a tree structure and like any tree structure it has a root (which is called Vadroot) and nodes/leafs (Vadnodes) that contains all the information related to memory ranges reserved for a specific process by the memory manager
source: VAD
We should consider where it has permissions. Let me cover about the permissions a bit.
These permissions give us an indication of the type of access. Lets analyze that with vad()
hmm…. EXECUTE_WRITECOPY
seems interesting. APT would use hidden directory of course however, ı
just want to demonstrate what kind of capabilities it has.
Enables execute, read-only, or copy-on-write access to a mapped view of a file mapping object. An attempt to write to a committed copy-on-write page results in a private copy of the page being made for the process. The private page is marked as PAGE_EXECUTE_READWRITE, and the change is written to the new page.
source : Microsoft
We can also use pslist() command to specify only the process
After this we can use regex method to find our malicios exe file.
Use this command: pslist(proc_regex="notepad") to filter malicious .exe
We can also dump DLL files with dlldump(proc_regex = "notepad")
We can also use threads() to specify win32_start_symb
As you see can it will be very useful to use regex_proc So far, we were talking about useful commands in Rekall terminal. Now let me write a simple how we can detect Notepadwith Rekall plugins.
Process Injection Detector Script
In order to write a correct script, we should be able to use Rekall’s plugins. Before diving into our script let me explain about this piece of code below:
First of all, we are going to be able to use pid and win32_start_symb to analyze our malicious process.
Here is the code. Do not worry I will explain my code step by step.
Automated Python script for Rekall
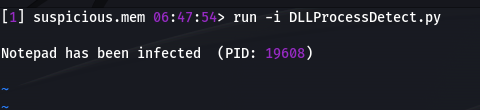
You can check my script: DLLProcessDetector.py
def process()
First of all, as we seen earlier that we need to dump process list because we already knew that we put our malicious DLL to Notepad.exe
but we have a problem. We know that the target is Notepad but as you can see in my code,if lsass
in the process, please continue
because it gives us some issues on Windows 11. Lsass, Local Security
Authority Server Service (LSASS) is a process in Microsoft Windows
operating systems that is responsible for enforcing the security policy.
if Notepad in the process then, send it to vad (virtual address Descriptor).
def vad()
Virtual address descriptor, this will be useful because it will give us the information about;
DLL files, memory protection, type, and more… so we parsed Notepad to vad. You can also check it via Rekall framework simultaneously.
If the given statements is true then, we will get True from that function. This means we can get the UniqueProcessId from that process.
def thread()
kernel32!LoadLibraryW, Loads the specified module into the address
space of the calling process. The specified module may cause other
modules to be loaded.
It will be very handy, if we can identify that this process uses
kernel32.dll after being executed.
If that is correct, and we are able to catch kernel32.dll then it will be placed in our dll_inject we are appending.
Lastly, we will print the result.
Output of my script
Summary
If you did like this memory Forensics with Rekall blog-post, please then not forget to share and like this blog. More awesome reverse and malware blogs will be appeared in this blog-site. If you unable to understand this concept, feel free to ask us for help.
Thank you for reading this blog.

0 comments:
Post a Comment