
Greetings to the best hacker in the world. Today, I am going to be writing Game Cheating Part 2
Today, what I want to cover will be about:
0x1. Nopping
0x12. Coding a simple NOP code.
0x2. Internal Hooking
It is recommend to read my first blog about Game Cheating part 1, because this blog will be the continue part.
I will also suggest you to look at the assembly part which is not written in my page, but you can check it out on Internet.
Let me get started with over-viewing the game. The first step is nopping the bullet amounts of the user.
Nopping
First of all, let me quick overview what NOP means. NOP or well (No Operation) means in Assembly, that it does not do any implementation into our code. In some cases, no-op instructions are used for timing purposes. They can also help to deal with certain memory issues, or work in conjunction with a group of other instructions to facilitate some kind of end result.
Please follow the instructions. After the instruction part, we will be automating into our code. It is always worth to learn and enhance your programming skills.
- Start your game.
- Start Cheat Engine.
- After starting two programs, please make sure that you attached the game to Cheat Engine.
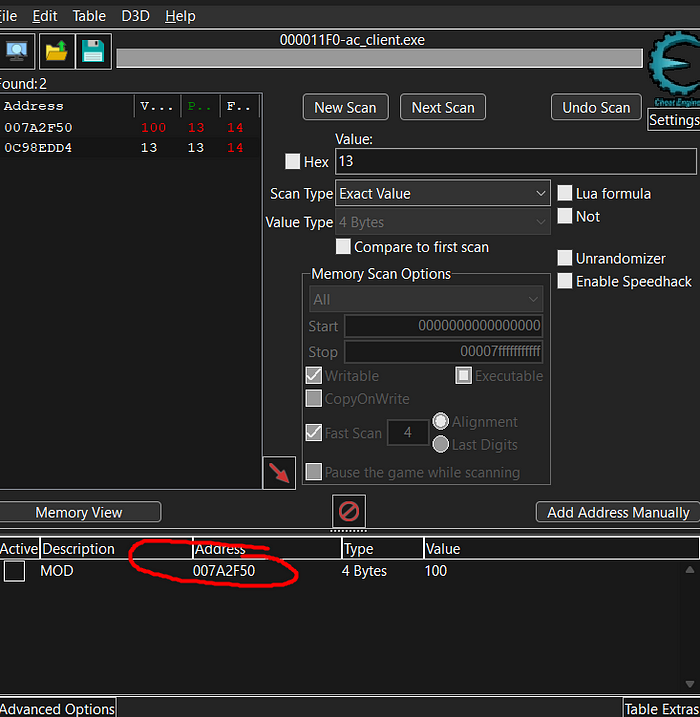
- When you attached the game, make sure that you shall look for the memory address of user’s bullets.
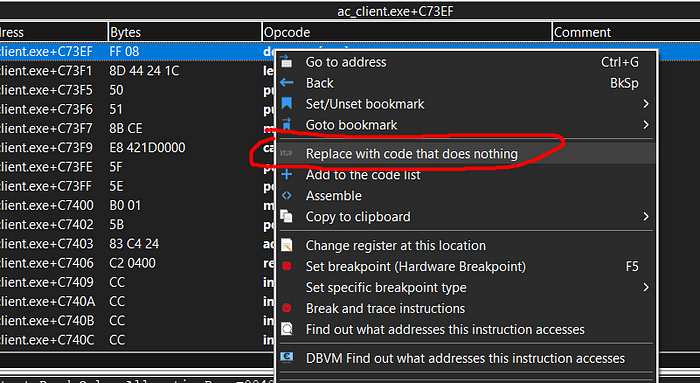
Please right click and go to >> “find out what writes to this address”
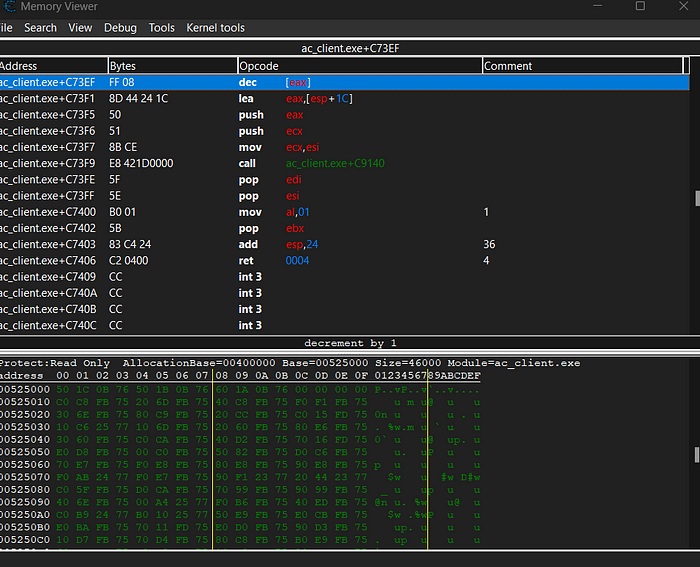
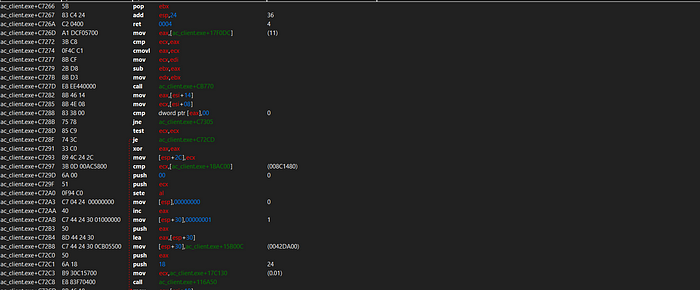
Debugging has started… Now, we are able to see when we shot once to the wall , the instructions of the code.
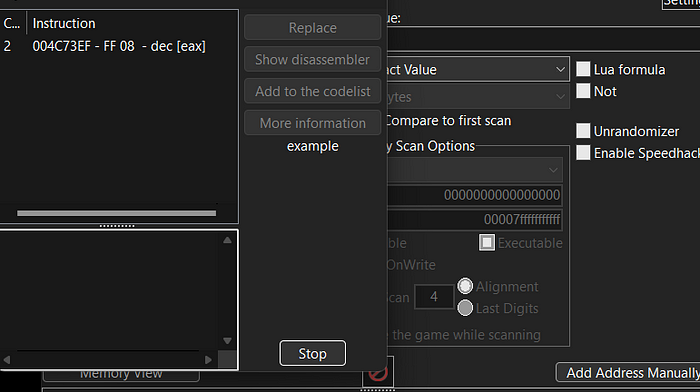
Now, we are going to disassemble our code to make it more understandable.
This is predictable because when we shot once, that means that it decrements 1 bullet from my weapon thus “dec” instruction will be in the game.
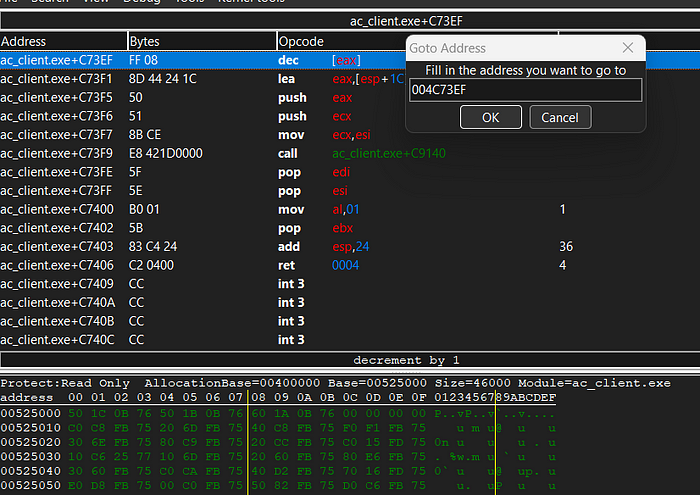
We are seeing that it does have 2 bytes, we can also check the current memory address to do so ; CTRL + g will be useful. We are also seeing that its a pointer address.
This information will be useful, because I am going to implement those information into my code.
If you click onto “replace with code that does nothing” this means just “NOP”
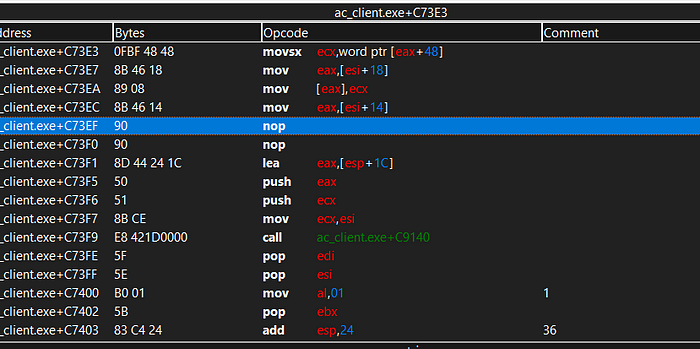
As you can see we were able to NOP the address.
You are not able to see, but when I am shooting the bullets are not decreasing because we just set as “NOP”
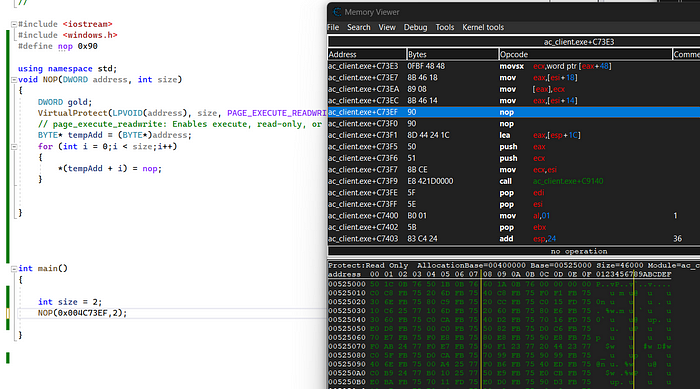
To learn and practice, we are going to write a simple code which automates it.
Coding a simple NOP address
I would recommend you to learn C++., if you are into reverse engineering and malware analysis. Let me get started to write a simple script.
First of all, we should understand that the code has been protected thus we need to manipulate it through “virtual-protect” API
To get more information about Virtual-Protection you can check: https://learn.microsoft.com/en-us/windows/win32/api/memoryapi/nf-memoryapi-virtualprotect
Virtual-Protection; Changes the protection on a region of committed pages in the virtual address space of the calling process.
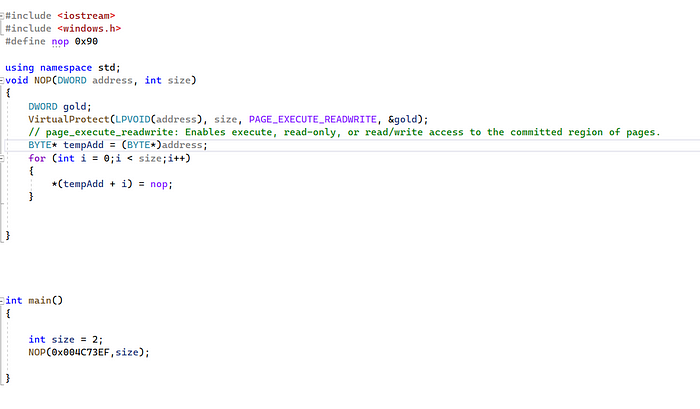
First of all, let me explain the source code.
- We should define “NOP” as x90 this means that instruction will be changed to nop operator.
2. As usual, we can create a function called NOP which holds the address and the size of bytes.
3. Virtual-protect will be important because we are not allowed to modify the source code, which should be able to use this API.
4. BYTE* = std::byte is a distinct type that implements the concept of byte as specified in the C++ language definition.
5. Gold does actually store the old protection previously.
Please do not forget to select > properties> and run as .DLL
Internal Hooking
Before illustrating the internal hooking part, let me introduce about API hooking.
API hooking is a technique where you can instrument and modify the API flow. Most EDR/AV are being used to determine the functions whether is malicious or not. We will be able to analyze and hook the functions.
Hooking can be used to introspect calls in a Windows application or can be used to capture some information related to the API Calls.
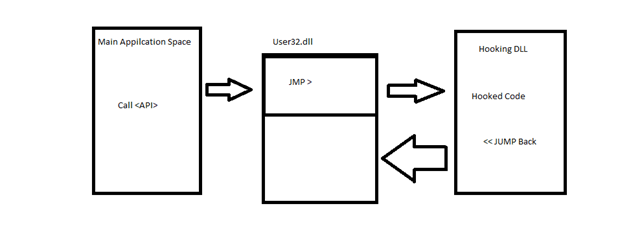
We can use trampoline method to modify and instrument the functions.
- First of all, as demonstrated above, it calls APIs from main application space
- Afterwards it will go into user32.dll to be jmped. (Windows management functions for message handling, timers, menus, and communications.)
- When the 2. phase is being done, then the code will be hooked and returns back to user32.dll.
Internal Hooking Code Instruction
First of all, let me start the game as well as Cheat-Engine.
Let me show the code before starting the process.
Awesome being disassembled code is given.
- Try to understand the functions (GOOGLE will be useful)
- After understanding the function calls, we need to implement our code to be called.
- We are going to use assembly language here…
We are going to manipulate these two parts…
Let me write a function called “FunctionManipulation”
Before writing the function, we will kick off with “_declspec(naked)” which means: the compiler generates code without prolog and epilog code. You can use this feature to write your own prolog/epilog code sequences using inline assembler code. It does not work on x64..
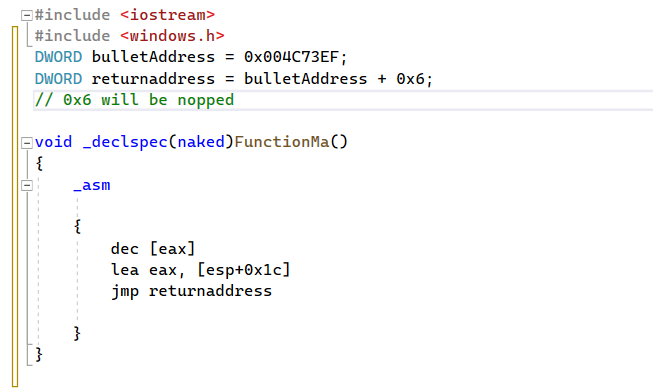
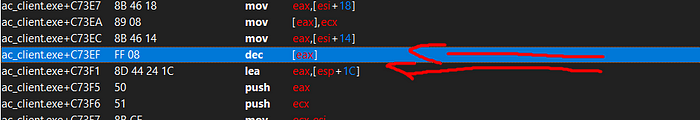
We will be manipulating the function. We need to delete 5 bytes from the code and only 0x6 will not be deleted, because this byte will call another function.
- Bullet address is known = 0X004C73EF (the memory address)
- return address is known = bullet address + 0x6 (the return address of 0x6)
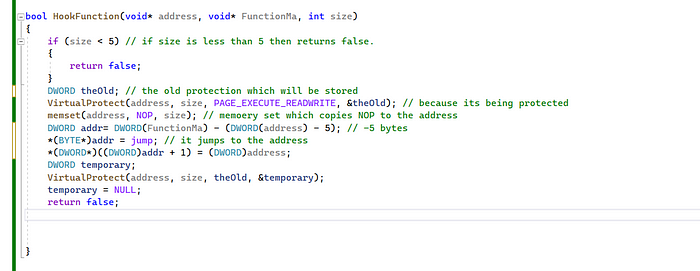
Now let me create a hook function
- If the size is less than 5, it returns false from that function.
- We need to declare the old protection which will be stored to the new VirtualProtect.
- VirtualProtect is declared (the address, the size, and the protection)
- memset; sets the first count bytes in c
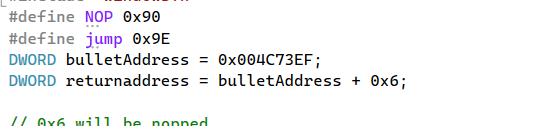
- NOP is declared as “0x90”
- jump is declared as “0x9E”
- Our current address is equal to the new address with +1 byte
- We should create our temporary protection to restore to virtualProtect.
Summary
Thanks for reading this blog. I will be going to learn more such techniques and writing to my blogs. Please stay tuned for more awesome hacking stuffs. Game cheating part 3 will be shared in soon.
Ahmet Göker | Reverse Engineer Jr

1 comments:
Nice!!
Post a Comment